Not long ago, supply chain security was mostly a back-office business topic — the purview of logistics managers, supply chain analysts, risk officers and IT professionals. COVID-19 changed that. After years of pandemic-related disruptions, the security and resiliency of supply chains is now front-page news and a top agenda item in board rooms across industries. Today, health crises are acknowledged as merely one of a multitude of threats to supply chain security and ongoing operations, which are also susceptible to cybersecurity attacks, intellectual property theft, geopolitical risks and natural disasters.
Thus, securing their supply chains has emerged as a top business priority in many industries, especially manufacturing, technology, retail and healthcare. This article examines the nature of supply chain security risks and the best practices for preventing or mitigating them.
What Is Supply Chain Security?
Supply chain security is an aspect of business operations management that focuses on mitigating risks related to external suppliers, vendors, logistics and transportation within a company’s network of supply. Securing the supply chain is a surprisingly broad remit, encompassing strategies for dealing with physical threats, cyber threats, transportation challenges, human error, malfeasance and, of course, software code. It’s also a growing problem, driven by two major forces: First, modern supply chains are much longer, geographically dispersed and digitally intertwined than they used to be. At the same time, they’ve become prime targets for cybercrime, intellectual property (IP) theft, counterfeiting and piracy.
There is no one-size-fits all approach to supply chain security because the threats and best approaches to mitigate them vary by industry and company. But there is broad consensus that a multilayered defense based on sound enterprise risk-management principles is the best strategy to protect supply chain networks without diminishing their performance.
Key Takeaways
- Modern global supply chains face a broad spectrum of security risks.
- Supply chain security professionals focus on identifying, analyzing, mitigating and responding to the full spectrum of security threats.
- The goal is to protect the flow of legitimate goods and services throughout a company’s network of supply without slowing down that flow.
- While there is no one-size-fits all approach, there are many best practices companies can adopt to bolster their supply chain security.
Supply Chain Security Explained
Supply chains have grown more global and more complex over time. Advances in technology and transportation, combined with falling trade barriers, have empowered companies to expand their sourcing options around the world. These longer and often leaner supply networks have created a host of benefits for businesses and their customers, including lower costs, greater access to materials and goods, and expanded markets. But the additional intricacy has brought greater vulnerability. Whether it’s a health crisis in a far off land that halts factory floor operations, a labor strike stopping rail freight, a flood that destroys warehouses, a geopolitical conflict squeezing shipping lanes or a cyberattack delivered through a widely adopted piece of software, any issue within a supply chain most likely will have cascading effects throughout the network.
Supply chain security is the management discipline meant to mitigate these threats and their ripple effects. As such, it requires implementing multiple types of security: cybersecurity, physical security, personnel security and procedural security. Done well, it involves close collaboration among suppliers, third-party logistics providers (such as ocean, sea, rail and road carriers, brokers and consolidators) and technology providers, among others.
While a high priority, improving supply chain security is still a work in progress for many businesses. Less than half (44%) of respondents to a 2022 survey by ISACA said they had high confidence in the security of their organization’s supply chain or its access controls. The crux of the problem is that supply chain security cannot simply lock things down. The efficient movement of goods throughout the supply chain is essential to businesses, economies and society. The goal, then, is to enable the flow of legitimate commerce through the network of supply while protecting the network from threats, complying with relevant government regulations and establishing incident response plans that lay the groundwork for rapid recovery when disruptive events prove unavoidable.
Why Supply Chain Security Is Important
Getting the right goods and services to the right place, at the right time and for the right price has become increasingly vital to business operations in recent years, as the velocity of the global economy has accelerated. When something goes wrong in a company’s supply chain, there are often significant operational, financial and reputational repercussions. At the same time, however, modern supply chains have become so vast and interconnected that the likelihood of security vulnerabilities has risen just as significantly. A cybersecurity attack, service disruption or other issue at one node can ripple through the chain, adversely affecting many other companies. Breaches within the system can lead to increased costs, delayed deliveries, poor customer experiences, IP or physical property loss, product quality issues and many other problems.
The interconnectivity and length of today’s supply chains makes securing them a nontrivial challenge. Many companies have found that while they may have detailed knowledge about the security and quality controls of their tier-1 suppliers, they have little or no visibility deeper into the network — at their suppliers’ suppliers, and their suppliers. This makes it very difficult for them to understand all of their digital vulnerabilities and to control who needs or has access to systems, assets and data.
That’s why investing in the right foundation of technology systems and controls is essential. While the various threats and vulnerabilities can’t be eliminated, companies can and are putting best practices in place to identify, analyze and manage these supply chain risks and respond more quickly and effectively to security incidents and disruptions. Evidence shows that this is not just a priority for supply chain leaders or logistic managers, but for executive teams as well. According to cyber defense services company BlueVoyant’s “2023 State of Supply Chain Defense” report, 44% of respondents said their senior management teams are briefed monthly, weekly or daily on supply chain issues, up from 38% in 2022.
Components of Supply Chain Security
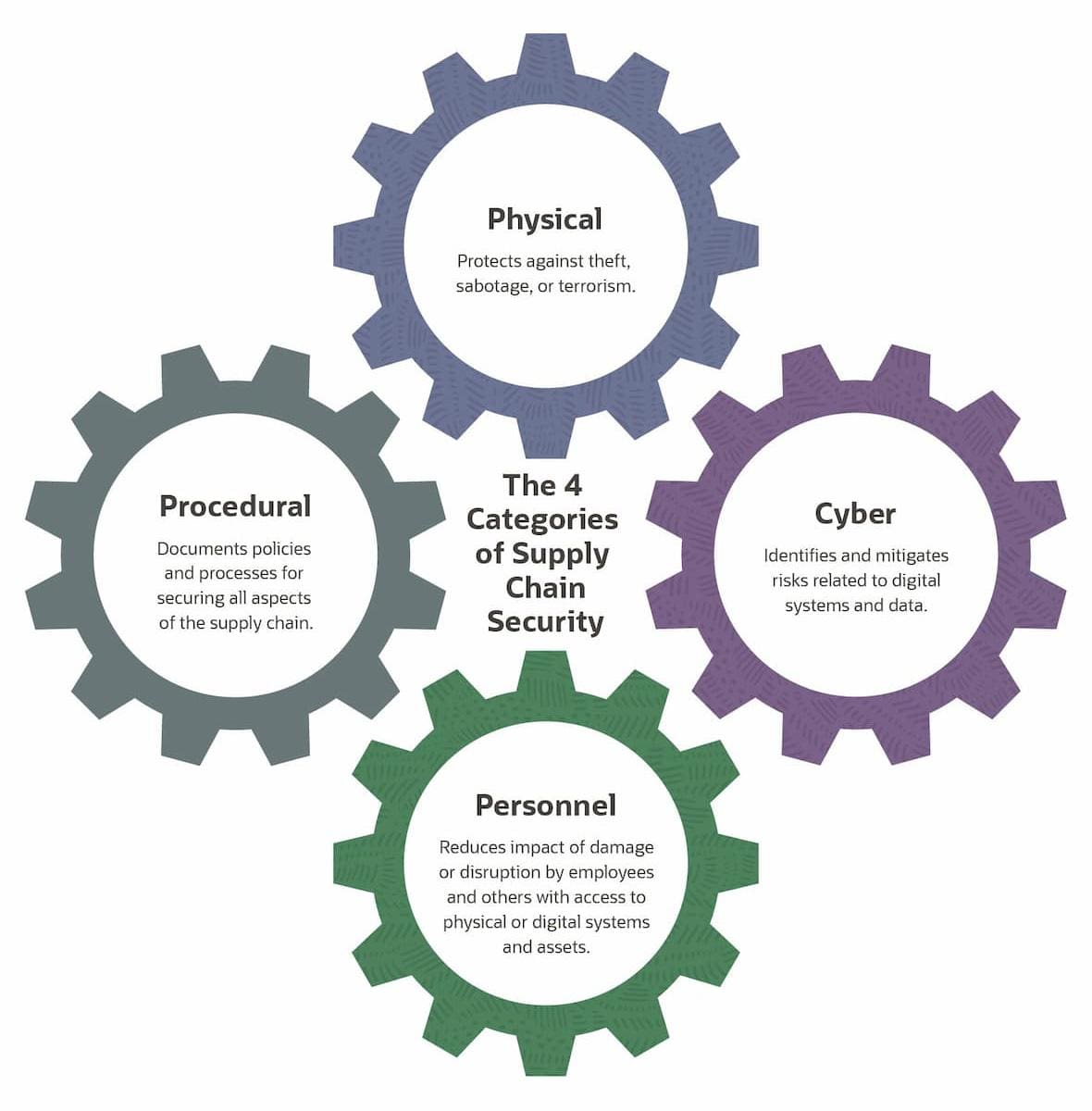
Supply chain security is multifaceted. It encompasses many categories of threats and risks, as well as the policies, procedures, technologies and controls a company puts in place to identify those threats, assess them and eliminate or mitigate them. Broadly speaking, there are four overarching components of most supply chain security strategies: physical, cyber, personnel and procedural. Essential to understanding these components is that none are meant to stand alone — they’re interconnected and interdependent.
-
Physical Security
Historically, supply chain security was physical security. Physical threats, ranging from theft and sabotage to terrorism, remain the most visible supply chain security risks. Organizations can mitigate physical attacks through physical protection, digital tracking and — believe it or not — maintaining regulatory paperwork. Accurate recordkeeping is indispensable, for example, to supply chain traceability, which can be key to maintaining physical security. Accountability, clearing customs and, of course, compliance with international regulations are also important.
Physical security most obviously interconnects with personnel security, because part of the physical security job is to keep people safe while they’re working in the supply chain. But it also links to cybersecurity, for example, because physical security measures, such as access controls and surveillance, protect against unauthorized physical access to IT infrastructure, such as servers and network switches. And cybersecurity systems, in turn, help protect physical assets by identifying and mitigating cyber threats that could lead to physical breaches.
-
Cybersecurity
Cyberthreats have become much more significant risks for supply chain security, and companies are paying commensurately more attention to how their suppliers manage those threats. According to a recent Wall Street Journal article, companies that once sent periodic questionnaires asking about their suppliers’ security practices are now demanding specific cybersecurity terms to be incorporated into contracts, such as adherence to the U.S. National Institute of Standards and Technology’s (NIST) Cybersecurity Framework(opens in a new tab). Concern is rising, in part, because a single breach or cyber incident in one of today’s long, interconnected supply chains could potentially affect hundreds of companies.
Cybersecurity in the supply chain focuses on third-party software and systems, the collaboration between businesses and their suppliers and resellers, and the shared data, networks and systems that are woven into supply chain networks. Cybersecurity controls should address vulnerabilities in IT and software systems, such as malware, account takeover and unauthorized access to key business infrastructure, such as enterprise resource planning (ERP) systems. Supply chain security professionals must also be on the lookout for negligent or malicious insiders who can open the door to cybercriminals, as well as to bad actors’ “backdoors” in commercial, open source or proprietary software.
-
Personnel Security
Humans are often the weakest link in — and biggest threat to — supply chains. Among the most important personnel security processes and policies are employee training (particularly cybersecurity awareness training) and screening, especially background checks. Other tools in the personnel security arsenal include access controls for sensitive areas or products (both physical and digital), exercises to test workers’ security awareness and response, the periodic review of roles with regard to supply chain access and communicating the importance of compliance with security practices to all members of a company’s supply chain.
-
Procedural Security
Procedural security is about all of the rules that govern the safety and integrity of supply chains, from a company’s high-level policies to its specific practices. As such, procedural security interacts with all of the other supply chain security components. It should include cybersecurity policies; processes for maintaining secure communication channels; designating security officers; procedures for moving goods; practices for detecting shortages, tampering and other malfeasances (as well as for notifying appropriate authorities); procedures for both planned and random security assessments and audits; contingency and response plans for specific incidents or disruptions; and clear steps for the ongoing identification and mitigation of supply chain risks. Importantly, these procedures should be both documented and verifiable.
The 4 Categories of Supply Chain Security
Supply Chain Security Threats
Keeping a modern supply chain secure and running at optimal speed and cost is no small task. There is no shortage of threats that can have an impact on the network of supply and, ultimately, a company’s costs, revenue, reputation and relationships. Understanding the primary threats to supply chain security and resiliency is the necessary first step in determining how to address them.
Some of the most common and impactful threats to supply chain security include the following:
-
Cybersecurity Attacks
Cybersecurity risk has long been on the rise, and cybercriminals are increasingly targeting suppliers in large companies’ supply chains. While digitally connected supply chains are a boon to costs, productivity and more, they also are catnip to criminals who recognize the opportunity to target multiple victims with less effort. Indeed, the average number of supply chain breaches that negatively impacted organizations increased 26% year-over-year to 4.16 incidents per responding company in 2023, up from 3.29 in 2022, according to BlueVoyant’s report.
As noted in another 2023 supply chain trends report from the Association for Supply Chain Management (ASCM): “The more digital supply chains become, the more vulnerable their global networks are to cyberattacks. This interconnectedness means supply chain partners can inadvertently expose each other and their customers to privacy breaches, identity theft and worse.” In a 2022 ISACA survey of 1,300 IT professionals with knowledge of the supply chain, ransomware was cited as a top supply chain risk by 73% of respondents, followed by poor information security practices by suppliers (66%) and software security vulnerabilities (65%).
-
Counterfeiting and Intellectual Property Theft
The multiple parties involved in global supply chains and lack of transparency within many of these networks increase the likelihood of IP theft and counterfeiting. Because supply chain traceability is still a work in progress for most companies, they cannot trace the full lineage of what they buy (e.g., raw materials or work-in-process inventory). So the possibility of purchasing counterfeit goods rises. And as companies work closely with supply chain partners to produce their products, they are often sharing highly confidential information (e.g., schematics for a new product) that are prime targets for IP theft.
The impact of IP theft and counterfeit goods costs companies in terms of lost revenue, loss of competitive positioning, reputational damage and increased warranty, liability and service costs. The U.S. Chamber of Commerce estimates that counterfeiting costs the global economy more than $500 billion every year. And the most recent calculation available from the FBI found that the combination of counterfeit goods, pirated software and trade secret theft costs the U.S. economy between $225 and $600 billion per year.
-
Supplier or Vendor Vulnerabilities
To better collaborate with suppliers, companies frequently allow them access to certain networks and systems. However, cyberattackers who get into that third party’s systems may then be able to use the access to infiltrate their customers’ systems as well. In addition, bad actors are increasingly targeting popular software and related software libraries as a way into many companies’ networks and data. So it’s essential that companies think about how they secure their software — the digital part of their supply chains. As stated in the Wall Street Journal article, “Every organization should be looking where their sensitive data is, if third and fourth parties have access to that data, and if those organizations have a good data classification policy.”
But for organizations that do examine their suppliers’ security practices, the results may not be comforting. As mentioned above, two-thirds of IT professionals familiar with supply chain practices said the poor information-security practices of suppliers was a top supply chain risk, according to the ISACA survey. A similar percentage (65%) said software security vulnerabilities were a top risk, 61% pointed to third-party data storage and 55% cited third-party service providers or vendors with physical or virtual access to information systems, software code or intellectual property. Research firm Cybersecurity Ventures predicts that the global cost of software supply chain attacks to businesses will hit $60 billion in 2025 and climb to nearly $138 billion by 2031.
-
Geopolitical Risks and Trade Conflicts
Recent headlines make clear the turmoil that geopolitical and trade conflicts can create in supply chains, from the Russia-Ukraine war’s stranding corn and wheat shipments to the Red Sea crisis causing cargo ships to chart new routes. Geopolitics was the No. 1 supply chain megatrend for 2024, according to a report from Resilinc, a provider of cloud-based supply chain security and resiliency services. Global politics affect supply chains in various ways, from inflating shipping rates, to restricting access to critical supplies and materials, to delaying or halting the movement of goods.
But while political instability, economic sanctions and territorial disputes pose significant risks to global supply chains, trade conflicts are generally the more common threat. Tariffs and retaliatory economic measures inflate prices and narrow profit margins. And both geopolitical events and trade conflicts lead to uncertainty, which challenges companies to plan and execute long-term strategies. The unpredictability of such disruptions can also strain supplier relationships and compromise the integrity of supply networks, forcing companies to develop robust risk management and agile response plans to maintain continuity.
-
Natural Disasters and Climate Change
Extreme weather events — floods, droughts, heat waves, wildfires, hurricanes, earthquakes — disrupt the flow of goods. In recent years, low river levels in Europe and drought in the Panama Canal triggered significant transportation disruptions whose ripple effects were felt throughout corporate supply chains. Worse, the frequency of these weather events and other natural disasters is rising with climate change. A 2024 University College London study, which was the first to consider climate change effects “cascading” through global supply chains, estimates that climate change will cause a net economic loss of between $3.75 trillion and $24.7 trillion (in 2020 dollars) by 2060, depending on how much carbon dioxide is emitted into the atmosphere over that period.
As the researchers explain: “Crop failures, labour slowdowns and other economic disruptions in one region can affect the supplies of raw materials flowing to other parts of the world that depend on them, disrupting manufacturing and trade in faraway regions.”
-
Insider Threats
While much of the focus of supply chain security is on mitigating security threats that originate outside of a company’s direct control, it’s important to mind the insider risks, too. In fact, many supply chain security incidents can be attributed to insiders, including employees, contractors and freelancers with access to corporate assets, systems and data. Some examples of supply chain insider threats include intentional malfeasance (e.g., employees stealing confidential data, damaging assets, stealing products or sabotaging systems), careless acts (e.g., workers falling for phishing attacks or leaving a warehouse door ajar), acts of compromise (e.g., someone whose devices or passwords are stolen, allowing access to sensitive data or systems) and disgruntled acts (e.g., insiders who intentionally do harm to the organization’s data, systems or supply chain).
-
Cargo Theft and Piracy
Cargo theft has risen to historic levels in recent years — and that’s only the portion that’s reported, which experts say is much smaller than the actual level. Nearly $130 million worth of goods was reported stolen in 2023, with individual incidents up more than 57% over the previous year, according to CargoNet, a theft prevention company. As one expert told CNBC, many criminals are embracing cargo theft because it offers high rewards with low risk. Criminals can access a greater volume of goods more easily by breaking into a cargo container or warehouse than by stealing from retail stores or individuals. Cargo theft and piracy can take various forms, from criminals who use bolt cutters to open locks on freight trucks and go “trailer shopping” to thieves who raid warehouses to steal prescription drugs destined for pharmacies and hospitals.
-
Quality-Control Failures
While quality — the ability of supply chain partners to reliably deliver products and services as specified — is a big deal, does it really belong on the list of supply chain security threats? Yes. Quality-control failures directly affect the integrity and safety of products, which is a critical aspect of supply chain security. Poor quality control can lead to the distribution of defective or contaminated products that can result in product recalls, legal liability and damage to a company's reputation. Furthermore, quality issues can indicate deeper supply chain vulnerabilities, such as substandard production oversight, which can be exploited by malicious actors.
Any number of factors can have a negative impact on quality control in the supply chain, from transportation problems and supplier issues to environmental factors and human errors. There’s even a metric for it: cost of poor quality (COPQ), which the American Society for Quality says can cost companies between 15% and 40% of revenue when counting the cost of having to appraise quality (e.g., verifying the quality of incoming materials and supplies); internal failure costs incurred to address defects discovered before the final product is delivered (e.g., waste, rework, failure analysis), and external failure costs for faulty or low-quality products delivered to customers (e.g., repairs, warranty claims, returns, complaints handling).
-
Regulatory Compliance Risks
Also lurking in company supply chains are significant compliance risks related to health and safety laws, labor regulations, export controls/sanctions and environmental, and social and governance (ESG) compliance requirements. Noncompliance with local, national or international regulations threaten supply chain security because it can result in legal and financial liabilities that disrupt operations and affect a company’s ability to conduct business. There is also the threat of outright fraud and corruption related to regulations and standards within the supply chain network. In some cases, a company and its executives, officers or directors may even be held criminally or civilly liable for infractions by their suppliers, such as failure to follow local labor laws, comply with ESG requirements or put necessary controls in place to protect data privacy.
-
Global Pandemics and Health Crises
Health crises and pandemics pose significant threats to supply chain security by disrupting operations at multiple levels. Companies around the world lived through the successive supply and demand shocks of the COVID-19 pandemic, which rocked supply chains across industries. Factory shutdowns combined with sudden spikes and troughs in customer demand revealed the fragility of global supply chains. Such is the general pattern of a health crisis’s impact on supply chains: First, workforce shortages due to illness, quarantine measures or travel restrictions decrease production and distribution capabilities. Second, changes in consumer demand create supply-demand imbalances. Third, governments may impose lockdowns or restrict the movement of goods and people, causing delays and bottlenecks at borders and ports. Furthermore, health crises can accelerate the need for improved health and safety protocols, requiring additional investments in technology and employee training.
Importantly, these types of impacts are not expected to be once-in-a-lifetime events. Companies must prepare for how future health crises might affect their supply networks and make contingency plans for how to deal with them.
-
Technological Reliance and Obsolescence
While advanced technology and tools can be invaluable in helping companies better secure their supply chains with greater visibility, automation and analytics, some legacy tools and processes can make matters worse. Unfortunately, supply chain operations have often been slow to digitally transform and embrace modern, cloud-based solutions. Companies that still operate using outdated ERP and supply chain systems that they customized over the decades now likely have messy code and unchecked vulnerabilities in their systems, leaving doors open to cyberattackers. Other companies operate using a hodgepodge of siloed systems that fail to offer end-to-end visibility and nothing close to real-time data or insight, which inhibits decision-making and prevents data sharing with supply chain partners. Some may have obsolete technology in place that’s no longer updated or supported by the vendor. Others still rely on manual or paper-based processes to manage their warehouses, logistics and supply chain operations. Any one of these situations not only leads to less efficient supply chain operations, but less secure supply chains overall.
Best Practices for Securing the Supply Chain
Naturally, supply chain security policies and approaches vary from company to company. It makes sense, based on the type and sensitivity of the business, as well as its priorities and risk tolerances. The crucial first step in any risk-management process is to identify, assess and prioritize the business’s threats, factoring in the likelihood and potential business impact of each. Because supply chain security intersects with multiple business functions, it’s also prudent to involve relevant stakeholders across the company in that exercise and in the development and application of new security processes, technologies and guidelines.
But while supply chain security should be customized to meet the specific needs of the organization, there are many common best practices likely to help most companies address supply chain security risks. From basic physical security measures, such as tracking shipments and applying tamper-evident seals, to cybersecurity controls, such as data encryption and role-based access permissions, these 14 practices work together to create a multilayered defense. They also help companies significantly enhance the resilience and integrity of their supply chains.
- Track shipments: Businesses can mitigate the impact of physical attacks
on goods moving through their supply chains by logging and tracking all shipments, with
automated notifications for both sender and recipient, when possible. Some companies may
invest in more sophisticated locating and tracking applications, like RFID tags and
scanners to monitor the movement of goods more easily (or work with third-party
logistics providers that do). Others may guard or check goods prior to or after shipping
to further prevent theft or tampering. However it’s done, real-time monitoring of goods
from origin to destination helps reduce theft, loss or damage, while maintaining
regulatory compliance. It increases accountability among carriers, enables quicker
responses to disruptions and can even improve customer satisfaction by providing
transparent order status updates. Finally, the data gathered by advanced tracking
systems can be used to help optimize supply chain operations.
- Apply tamper-evident seals: Tamper-evident shipping seals or locks add
another layer of protection for goods or packages, ensuring that their integrity remains
intact as they work their way through the supply chain. Seals or locks can deter
unauthorized opening of packages, whether they’re being held in a storage room,
warehouse, on a vehicle or in some other facility. Tamper-evident packing materials,
such as shrink bands, induction seals or tape, can serve as an alert that items may have
been manipulated and should be checked or taken out of the supply chain.
- Regularly inspect warehouses and factories: Companies that want
to ensure the security of their inventory, assets and operations will
want to inspect their warehouses and factories on a regular cadence. Warehouse
inspections are of particular concern for any companies that hold or sell perishables or
regulated products that can cause safety concerns if not handled properly. In fact, the
U.S. Food and Drug Administration enforces compliance with inspections to make sure the
warehouses that store goods under its purview meet regulations. Companies may also
invest in external auditors or inspections to check that their security protocols and
processes are in compliance.
- Mandate employee background checks: Background checks are an important
measure to help prevent bad actors from accessing secure facilities, sensitive
information, valuable products or high-risk materials. Some buyers mandate background
checks on any supplier employees who work in their supply chain, and some checks are
mandated by the government. Truck drivers, for example, must pass background checks to
operate at ports and maritime facilities. Warehouse workers must pass a background check
again to be eligible to handle biomedical equipment or hazardous
materials.
- Partner with certified suppliers: The two most common standard
certifications relevant to supply chain practices are International Organization for
Standardization (ISO) 9001, which demonstrates a supplier’s commitment to certain
standards for quality assurance, and ISO 14001, which demonstrates a supplier’s
commitment to standards for environmental responsibility. But there are many others,
from ISO, national governments, trade and professional associations, individual
businesses (that certify competence in configuring or repairing their products, for
example) and right down to business licenses issued by local jurisdictions. Working only
with certified suppliers takes some of the guesswork out of supply chain sourcing and provides
reassurance when it comes to
quality, risk mitigation, regulatory compliance, continuous improvement and overall
performance.
- Evaluate and update security strategies: A comprehensive supply chain
security strategy should be built on risk management and cyber-defense in-depth
principles and address any regulations or protocols established by government agencies.
It should also be a living document — one that is reviewed and revised regularly because
supply chain threats, particularly cybersecurity risks, are constantly evolving. As a
result, a company’s supply chain security strategy must keep pace with a changing threat
environment.
- Conduct penetration tests and vulnerability assessments: Vulnerability
assessments bring supply chain cybersecurity risks to light, particularly the
lowest-level opportunities that threat actors might exploit, such as insecure database
configurations, weak password protocols and unprotected networks or endpoints. Then the
organization can harden these weak points. Hiring a third party to conduct penetration
testing can help to identify more advanced threats within the supply chain. It’s also a
best practice to confirm that key partners and suppliers with which the company shares
data or systems also perform regular vulnerability assessments and penetration tests and
check on their results regularly.
- Authenticate and encrypt all data transmissions: NIST says businesses
should establish security controls based on the idea that data breaches are inevitable.
Therefore, organizations should establish priorities and protocols for every type of
data they transmit, store or share. It’s important that companies secure data
transmissions to supply chain partners using a data encryption method that aligns with
their needs, and that they authenticate any data coming into their organizations from
partners (verifying the data and its origins). If supply chain partners use online
platforms to access data, advanced controls, such as multifactor authentication, digital
signatures or session breaks, should be used.
- Set role-based access controls: Identity and access management (IAM)
security practices provide essential protection because they enable permission- or
role-based data access. Many companies find it helpful to adopt the principle of least
privilege, which states that users (or applications and systems) only have the access
and permissions that are necessary for their role. Minimizing access restricts the
damage that any compromised user, supplier or application can cause to the organization.
Many companies layer this with ongoing monitoring of access to identify and resolve
potential issues quickly.
- Ensure vendors meet cybersecurity standards: Requiring minimum
cybersecurity controls from vendors and resellers is a rapidly growing best practice.
Developing a robust third-party cyber-risk management program can help companies assess
their supply chain partners’ cybersecurity posture and practices and better collaborate
with them on strengthening shared defenses. In fact, 85% of respondents to the
BlueVoyant report stated that their budgets for managing third-party risk had increased
over the past 12 months. In addition, 47% of respondents said their organizations
monitor their supplier/vendor risk at least monthly, up from 41% who said so in
2022.
- Audit source codes from open-source and commercial vendors: Supply
chain security should also incorporate mitigating the risks that come from using
third-party software, whether purchased from a commercial software company or accessed
in the open-source community. It’s never safe to assume that any piece of software is
secure. Cybercriminals commonly target open-source libraries and vulnerabilities in
widely adopted enterprise systems to expand their potential attack surface. Regular
audits of open source and vendor source code can help companies identify and remediate
vulnerabilities or backdoors. Companies can also perform various types of application
security testing to look for dependencies within the applications they
use.
- Use network scanning and intrusion detection: Investing in
network-level scanning, intrusion detection and behavioral analysis of users (to
identify possible insider threats) can be invaluable for spotting potential
cybersecurity breaches and addressing vulnerabilities. Some companies also opt to
increase their defenses by dividing company networks into multiple segments, making it
more difficult for cyberattackers to move through the network and easier for security
analysts to detect them.
- Create response plans for security threats: As NIST stipulates, even
with the best-laid plans some security issues are unpreventable. So defense is only half
of a supply chain security solution. The other half is being prepared to respond when an
issue arises, whether that’s a ransomware attack, a supplier quality issue or a
logistics provider labor strike. That means creating a well-thought-out, communicated
and practiced incident response plan for each major category of disruption. The
investment will pay off immediately when the organization is able to react to a problem
quickly and effectively, minimizing revenue loss, downtime, reputational damage and
partner or customer churn. Incident response plans should make sure that everyone knows
what to do in such situations and does not inadvertently exacerbate the disruption and
its impact.
- Follow governmental security regulations: While some aspects of supply chain security are optional, based on the needs and goals of the business, government regulations or mandates and industry-specific rules clearly are not. And given that most companies are now working within global supply chains, there are many national, regional or local regulations that will need to be understood, monitored and complied with, as noncompliance by a company or its partners can result in significant fines or even shutdowns. Keeping on top of regulatory supply chain requirements and auditing compliance plays a key role in overall supply chain security.
Secure Your Supply Chain With NetSuite
The best supply chain security solutions require visibility throughout the entire network of supply. So it’s no surprise that a recent survey of supply chain professionals found that end-to-end visibility was their top investment priority. NetSuite Supply Chain Management is a modern, cloud-based supply chain management solution that can provide that visibility by natively integrating with the entire NetSuite range of business management and financial/accounting ERP modules. Just as important, NetSuite can serve as a foundation for more robust supply chain security.
NetSuite helps business leaders identify security risks, plan contingencies and address weaknesses before they become major issues for supply chain operations. Sophisticated demand forecasting, supplier visibility, inventory management, predictive analytics and scenario planning gives supply chain leaders, logistics managers and executives the tools they need to prevent and respond to supply chain risks and disruptions. NetSuite’s centralized solution also enables companies to share data easily and effectively with key partners in their supply networks so that everyone is on the page and can quickly communicate and collaborate to address new challenges as they arise. And the cloud-based solution means that decision makers can access key data and insight anytime, anywhere to keep their supply chains moving.
Protecting the supply chain and managing associated risks is highly complex and challenging, but companies can take clear steps to better understand and prioritize threats. They can institute cyber, physical, personnel and procedural controls, and mitigate and manage their risks using supply chain security best practices. With the right technology, processes and training, companies can strengthen their supply chain security posture and evolve their supply chain strategy and plans to keep pace with a dynamically evolving threat environment.
Supply Chain Security FAQs
What are the different types of supply chain security?
Supply chain security involves not only physical security, but also cybersecurity, personnel security and procedural security. While there is no one approach to supply chain security that applies to all companies or industries, it’s generally a best practice to develop a multilayered strategy based on risk management principles. Some common aspects of supply chain security plans include tracking and monitoring shipments, inspecting and auditing warehouses and factories, conducting employee background checks, controlling digital and physical access, conducting vulnerability assessments and penetration tests, assessing the security of all vendors and partners, and developing incident-response plans.
What is supply chain in cybersecurity?
Within the realm of cybersecurity, the term “supply chain” is typically used to refer to the digital supply chain: the third-party systems a business relies on for its operations. Digital (or cyber) supply chain security is itself a subset of supply chain security that is focused on bolstering the cybersecurity of systems, software and networks. Some common best practices for securing the digital supply chain include buying from trusted or certified vendors only, integrating cybersecurity requirements into all contracts and statements of work, auditing source codes from open-source and commercial vendors, investing in network scanning and intrusion detection, and providing cybersecurity awareness training and testing for all users.
What are the objectives of supply chain security?
Today’s complex and global supply chains create many categories of risk that companies must work to identify and mitigate, including cybersecurity attacks, intellectual property theft and counterfeiting, supplier and vendor vulnerabilities, geopolitical and trade risks, natural disasters, insider threats, cargo theft, technology issues, compliance risks, global pandemics and quality-control failures. The goal of supply chain security is to enable the ongoing flow of goods and services while mitigating and being prepared to respond to these common risks.
What do you mean by supply chain security?
Supply chain security is an aspect of supply chain management devoted to protecting the flow of legitimate commerce and data from various threats and disruptions. Those involved in securing a company’s supply chain are tasked with identifying, analyzing and mitigating risks inherent in its network of supply. Because many of the vulnerabilities in a company’s supply chain are outside of its direct control, effective supply chain security requires collaboration with many different third parties and the establishment of response plans for dealing with various potential disruptions within the network.