Ensuring that the right people have the right permissions to access the right data is critical for a business's information security, as does identity management. The open, industry-standard Lightweight Directory Access Protocol (LDAP) helps businesses do exactly that. It's the main communications method for querying technology systems' directories of user accounts, groups and networked devices. It's often used to authorize or authenticate that people are who they say they are, and to determine the permissions they have to access information, applications, printers and whatever else is present on the organization's network.
What Is LDAP (Lightweight Directory Access Protocol)?
LDAP is an open, industry-standard protocol, originally developed in the early 1990s, that specifies how directory servers store and arrange data about users, services, applications and more over an internet network — a network that uses the Transmission Control Protocol/Internet Protocol (TCP/IP, or simply IP). TCP/IP, LDAP and many related specifications are all voluntary internet standards produced and published by the Internet Engineering Task Force (IETF).
LDAP makes it easy to search such directories for users and networked devices without knowing exactly where on the network they are or all the relevant information about them. It's also a mechanism by which software programs can interact with directories, and so is used to automate security processes like authorization and authentication. For example, a company network whose applications and devices are all compliant with LDAP could provide a business manager with access to everything with a single sign-on.
What Does 'Lightweight' Mean?
Many tech industry products and standards come with names that are related to something else. The UNIX operating system, for example, was so named because it was intended to be the opposite of MULTICS, an influential but now forgotten early mainframe OS. That's also the case with LDAP. LDAP is "lightweight" relative to the Directory Access Protocol (DAP) written into X.500, the first standardized directory service included as part of the seven-layer Open Systems Interconnection (OSI) model. DAP required the OSI protocol stack. LDAP was designed to be a lower-code — or "lighter" — way to access X.500-type directory services via TCP/IP, which is far simpler than the OSI protocol stack.
Key Takeaways
- LDAP is an open, industry-standard protocol that provides a way for directory servers to store and arrange data, and to handle queries about that data.
- LDAP can be used to authenticate users, ensuring they are who they say they are, and to authorize their access to specific data, applications and network devices.
- LDAP is often compared to Active Directory, Microsoft's proprietary directory services platform. But LDAP is a product-agnostic protocol that is incorporated into Active Directory and many other directory services.
LDAP Explained
As the internet rose to prominence in the early 1990s, along with its fundamental protocol, TCP/IP. Businesses began switching their internal networks from a variety of different network protocols, which were often proprietary to one company, to TCP/IP, which was (and remains) a public standard. Those company networks required directory services, which became standardized for TCP/IP in LDAP beginning in 1993. The current version, LDAPv3, was published by the IETF in 1997.
Interestingly, LDAP's ancestry goes back to the telecommunications industry and its long history of developing telephone number directories. The International Telecommunications Union (ITU) developed the OSI model's X.500 specification to mimic — for computer networks — the functionality of a telephone directory. LDAP was, ultimately, derived from X.500.
How Does LDAP Work?
LDAP is based on a client-server model: LDAP-enabled servers make stored information accessible to LDAP clients. A client (which could be a user account, a network service, an application or a device) "binds" to the server, meaning it authenticates itself. The client then sends an operation request to the LDAP server seeking specific information. The LDAP server, which is often instantiated in a directory services platform such as Microsoft Active Directory, processes the query and provides a response. When the client receives the response, it unbinds from the server and processes the data.
LDAP directory entries are stored in a hierarchical, branching structure descending from a single "root." At the top of the hierarchy are entries representing the largest groups, with groups getting progressively smaller as they move down the hierarchy. In LDAP, the branches are labeled as:
- Countries, which have
- Organizations, which have
- Organizational Units, which have
- Individuals (besides people, shared network resources such as printers, files and storage volumes are all called Individuals).
Each entry in the LDAP hierarchy is identified by a distinguished name (DN). The DN uniquely identifies the entry at its level in the hierarchy and the path that traces the entry back to the root. Each entry also has a relative distinguished name (RDN), which is the last element of its "path," in the same way as a filename is the last element in a file system path or a web page name is the last element in a URL.
Clients can make changes to the LDAP database — such as adding and deleting entries, as well as updating and renaming them — by establishing a connection to the LDAP server using a client utility. Once a change is made, all clients see it immediately.
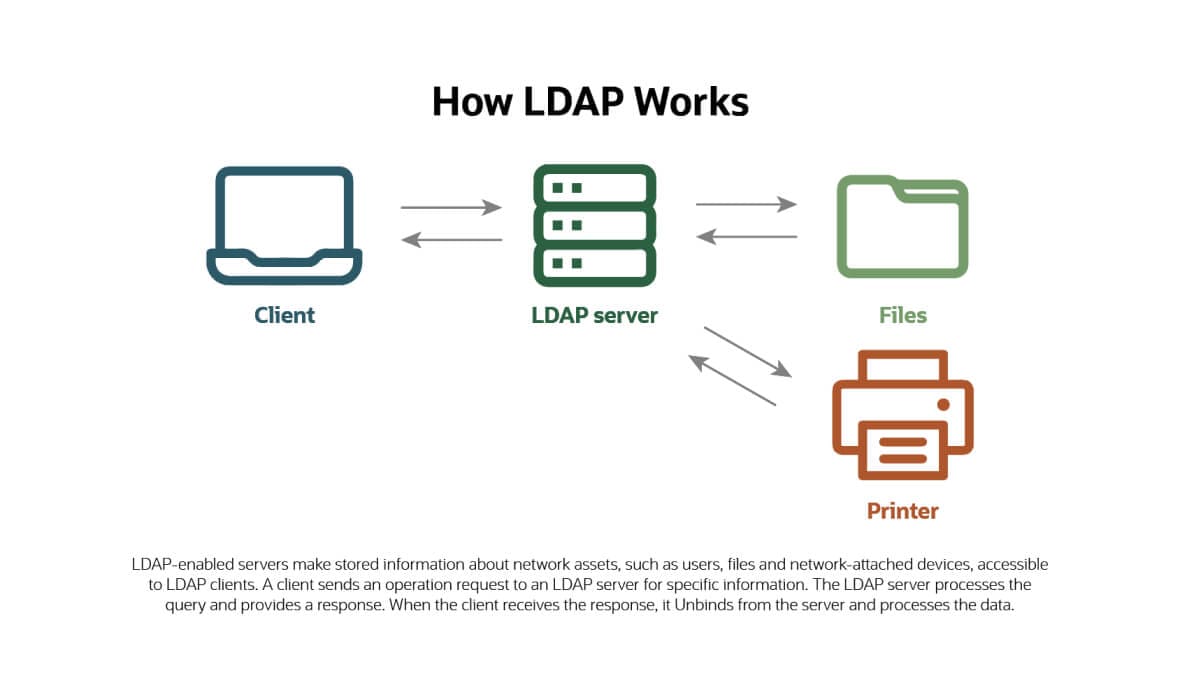
How Does LDAP Authentication, Authorization and Access Control Work?
To access information or network resources via LDAP, clients (technically called Directory User Agents, or DUAs) must go through an authentication process that involves sending a request to the LDAP database. The LDAP server checks the submitted credentials — such as username and password — against identity data stored in its database, granting access if there is a match.
The result of that authentication process tells the LDAP server what information and network resources the client is authorized to access. LDAP access control capabilities restrict the resources users get access to and what type of access they get to those resources.
Uses of LDAP
Organizations commonly use LDAP as a central place to store usernames and passwords, which leads to the important role LDAP plays in cybersecurity. But LDAP-enabled directories can also store email addresses, job titles, telephone numbers, printer connections and other static data. Because LDAP is an open, vendor-neutral protocol, it is supported by many different applications and platforms that can access that data to automate various processes.
A prime example is the use of LDAP as a hub for authenticating users and authorizing their access to a company network. Since advanced cybersecurity technology takes into account information about a company's employees, such as their role in the organization, many security systems initially "learn" that information by interacting with LDAP-enabled directories, primarily Microsoft's Active Directory.
LDAP is also used to manage user access to IT resources such as databases, applications and printers.
Why Do Businesses Use LDAP?
There are many reasons why organizations continue to use LDAP for authentication, even while other, more recent alternatives emerge. Importantly, LDAP is an open-standard protocol supported by a wide variety of applications and platforms. This enables an organization to use LDAP across many different applications and platforms and helps avoid vendor lock-in.
LDAP is also relatively versatile. Not only can it be used to store key organizational attributes, such as usernames and passwords, but it can also be used to store information on organizational structure and network-connected assets. This makes it easier to manage and protect user identities, and ensure that employees can easily access all of the tools they need to effectively perform their jobs.
LDAP Models
LDAP models describe the services provided by an LDAP server. According to the book "Understanding and Deploying LDAP Directory Services," there are four models:
-
Information model:
This model provides the structures and data types necessary for building an LDAP directory information tree (DIT).
-
Naming model:
Each entry in a DIT has an attribute — known as its relative distinguished name (RDN) — that is unique. The naming model defines how the entries are uniquely referenced.
-
Functional model:
The functional model is the LDAP protocol itself. It enables clients to access data in the DIT and is implemented by LDAP's authentication, query and update operations.
-
Security model:
The security model enables clients to provide information about who they are (authentication) and the server that controls an authenticated client's access to data and services (authorization).
LDAP Operations
LDAP's functions are instantiated in 10 basic operations, all of which can lead to multiple results, depending on what additional functions or attributes are specified when the client requests the operation. But there's more: Because LDAP is open and extensible, the 10th operation enables developers to create new LDAP operations that weren't envisioned in 1997, when the current version of the specification was published. The 10 core LDAP operations are:
-
Bind, which is used to authenticate a client and the user or application behind the client. It establishes the client's identity and associated permissions/access privileges for all subsequent activities processed by the LDAP server during that session.
-
Search, which retrieves entries from the LDAP database that match a given set of parameters.
-
Compare, used to determine whether a particular entry in the LDAP database has a specified attribute value. If there's no match to an existing entry, Compare returns "noSuchObject"; otherwise, the result would usually be either true (the entry has the specified attribute) or false (it doesn't).
-
Add, which lets IT administrators create a new entry to an LDAP-enabled directory.
-
Delete, which, naturally, lets you remove an entry from the directory. Usually, it must be a "leaf" — an entry with no subordinate entries. But some LDAP server policies allow deletion of an entry and all its subordinates.
-
Modify, which lets you alter the content of an entry. One Modify operation can change multiple attributes of the same entry, processed "atomically" — which means, if any one of the modifications fails for any reason, they all fail. Modify cannot change the DN (name) of the entry.
-
Modify DN, which must be used to change the DN of an entry, including moving the entry to a different level in the directory tree. Modify DN lets admins rename entries that have subordinate entries, but policies can be set to prevent it.
-
Unbind, which — despite its name — does not simply revert the bind operation. It is a signal from a client that tells the LDAP server that the client plans to close its session. It's technically a "courtesy," because LDAP servers are capable of handling situations in which the client simply disconnects without sending an unbind signal. But it's recommended because, without it, the server won't know for sure whether the client meant to disconnect or if there was a network issue, for example.
-
Abandon, which tells the server that the client no longer needs the results of a previously requested operation, so the server can stop it. Clients sometimes no longer need such results because LDAP is an asynchronous protocol, which means clients can send many requests that may be responded to in a different order than that sent.
-
Extended, which denotes a new operation created by a developer or a user organization. Anyone who learns enough about LDAP's language and syntax can create new operations that can be kicked off via the Extended operation.
Active Directory vs LDAP: What's the Difference?
LDAP is often compared with Active Directory, the directory services platform from Microsoft. But it's not an apples-to-apples comparison: Active Directory is a proprietary directory service that uses LDAP (among other protocols, such as Kerberos, for higher-security authentication).
What Is Active Directory?
Microsoft Active Directory stores information about objects on the network in a way that makes it easy for administrators and users to find the information they need. Active Directory uses a structured data store and organizes directory information hierarchically. Active Directory's structure is based on domains (a logical group of network objects, such as devices or users), trees (hierarchical collections of domains) and forests (hierarchical groupings of trees that share the same global catalog and directory schema). Objects in the data store include shared resources, such as servers, volumes, printers and network user and computer accounts. Logon authentication and access control provide integrated security in Active Directory.
Key Differences
When comparing LDAP-enabled servers (that is, directories that leverage LDAP as a primary means of communication) with Active Directory, it is useful to think about use cases for context. For example, LDAP servers are well suited for very large scale operations and/or situations in which multiple authentications are required. Active Directory, on the other hand, scales well when an organization is distributed into multiple forests and domains, but not as well for large implementations with a single community of users. When it comes to securing Microsoft Windows systems specifically, Active Directory and its Group Policy have a distinct advantage over a different LDAP-enabled directory, due to the tight integration between domain-joined Windows computers and Active Directory.
Benefits of LDAP
LDAP's main benefit is also its raison d'être: As an open protocol, it enables organizations to consolidate authentication across many different applications, platforms and vendors. But since LDAP databases have many uses beyond authentication, it can reduce the number of different databases an organization must manage by replacing multiple application-specific databases with a single LDAP-enabled database. Beyond that, LDAP's benefits are largely technical: LDAP can read data out of very large databases faster than most similar systems, and it usually supports more frequent data synchronization so that mirrored information remains in sync. It has a very well documented application programming interface (API), which makes it easier for developers to create LDAP-compliant applications.
Disadvantages of LDAP
The main disadvantage of LDAP lies in its inherent security — or relative lack thereof. This is ironic, because LDAP is an important element of many organizations' cybersecurity infrastructure. This seeming paradox emerges from the fact that, while the type of data LDAP-enabled servers store is highly sensitive, LDAP traffic is not encrypted. All information, including usernames and passwords, are transmitted as clear text by default. LDAP servers, therefore, are both attractive targets and vulnerable to man-in-the-middle and eavesdropping attacks.
Organizations can make LDAP more secure by adding transmission encryption, such as Transport Layer Security (TLS). You’ll often see TLS referred to as SSL/TLS, because it's the same thing — TLS is the successor to Secure Sockets Layer (SSL), the original encryption standard for client-server internet communications that is no longer used. Microsoft, for example, has created a TLS-based extension for LDAP connections to Active Directory that it calls LDAPS, for Secure LDAP.
LDAP and Security
LDAP provides a layer of security through its authentication and authorization capabilities. However, LDAP systems store some of the most sensitive information in the organization, which makes them a target for hackers. There are several best practices that organizations should put into place to ensure the security of LDAP systems. For example, organizations should configure LDAP systems to set conditions on passwords (such as requiring complex passwords and/or requiring that users adopt multifactor authentication). Organizations should also make use of encryption, such as SSL/TLS, and put systems in place to guard against LDAP phishing and spoofing — cyberattack approaches in which a malicious actor masquerades as an organization’s LDAP server to steal user credentials or other information.
LDAP Authentication
To access information stored inside an LDAP database or directory, users must first prove their identity. That authentication involves providing credentials when attempting to initiate a connection (Bind). Steps in the authentication process include:
- A client sends a request to access data stored within the LDAP-enabled directory.
- The client provides credentials.
- The LDAP server checks those credentials against data about identities stored in its database.
- If there is a match between the credentials and a stored identity, the client can access the requested information.
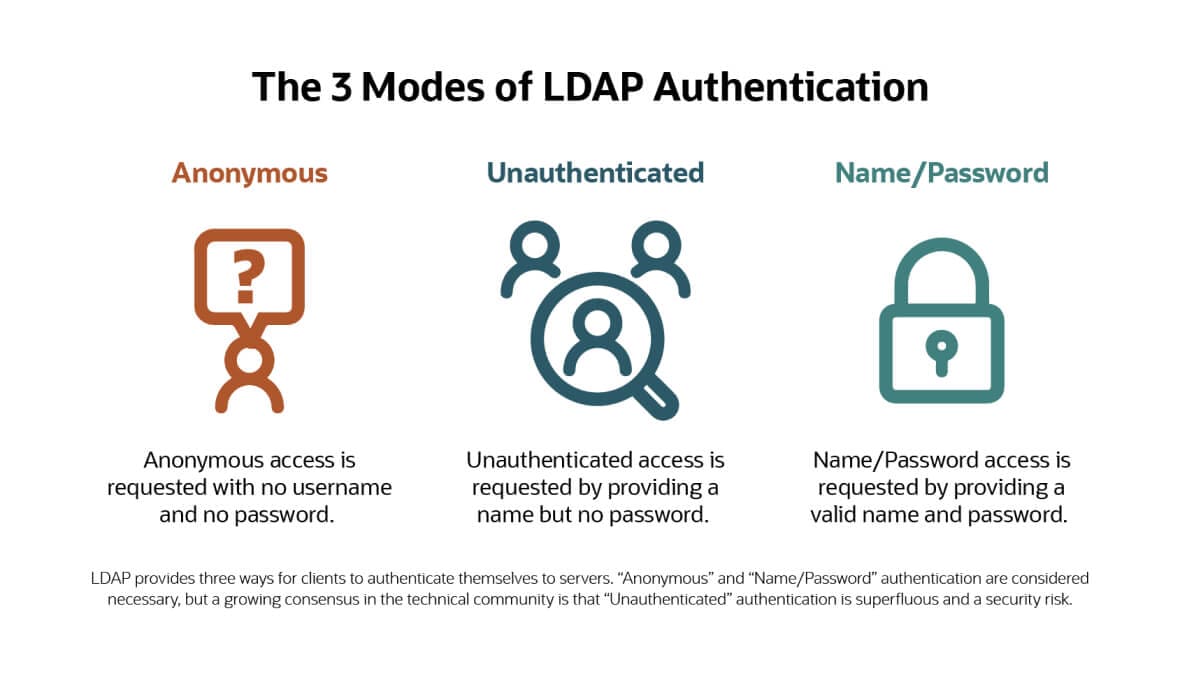
The LDAP Bind operation supports three "Simple" authentication results, plus an additional approach called Simple Authentication and Security Layer (SASL). The three Simple results are:
-
Anonymous authentication:
The anonymous Bind results when no username and no password are provided by the client. It's necessary for an initial contact in which the client gets information about what services the LDAP server provides. It can also be used to provide access to public information, similar to the way a visitor accesses public content on a corporate website.
-
Unauthenticated authentication:
This oxymoronic Bind results when the client provides a username but no password (i.e., a "zero-length password"). Its stated purpose in the original LDAP specification was "for trace (e.g., logging) purposes only." However, it's now considered dangerous, because applications that are unaware of this unusual function may assume a user has authenticated with a legitimate password and grant them access based on the LDAP Bind, thus opening a potential hole for hackers. The current specification recommends it be disabled by default.
-
Name/password authentication:
A client gets this Bind by providing a valid name and password. A successful Bind using these credentials results in full user authorization, according to the permissions granted to their identity within the LDAP-enabled database.
SASL, as its name implies, adds an extra layer of security to LDAP authentication and authorization mechanisms. SASL is a standalone authentication standard published by the IETF that allows for many different encryption schemes, including TSL and Kerberos. Details for how to use SASL in connection with LDAP-enabled databases and applications are written into the LDAP standard.
Conclusion
When it emerged in the late 1980s and early 1990s, LDAP provided an innovative — and publicly standardized — way for IT networks to authenticate users, thus providing identity and access management capability across many different systems, applications and devices. LDAP became ubiquitous and today it still forms the foundation for many directory service systems. Further, its identity and access management functions remain the central hub for many companies' cybersecurity systems, even as vendors and organizations up the authentication ante to the point of "zero-trust" to battle ever more sophisticated cyber threats.
LDAP FAQs
What is an example of LDAP?
Since LDAP — the Lightweight Directory Access Protocol — is an open standard specification for communicating with a directory database that has been in popular use since the mid-1990s, there are abundant examples of LDAP-based products from many computer and software makers. The LDAP example in most widespread use is Microsoft's Active Directory.
What is the difference between LDAP and SSO?
LDAP is a standard communications protocol for communicating with a directory database, and is typically used to provide identity and access management across many different IT systems, applications and devices. SSO stands for single sign-on, and is a process by which an individual can sign on to a corporate network once and gain access to all the network resources they have permission to use. Since LDAP-enabled directories maintain databases of user identities and their associated permissions, SSO processes often work collaboratively with LDAP servers to access that information.
What is the difference between LDAP and SAML?
Emerging in the early 1990s, LDAP is a standard communications protocol for communicating with directory databases that can be used for multiple purposes, of which authentication and authorization for single sign-on is one. SAML — the Security Assertion Markup Language — emerged about a decade later, is entirely focused on single sign-on, and is designed to work in the cloud. SAML can authenticate users for access to applications and resources, across multiple corporate domains, via a web browser over the internet.
What is LDAP authentication?
LDAP authentication is the process of ensuring that users requesting information from an LDAP directory or database are who they say they are. This process involves providing credentials when attempting to connect to a directory service that uses the LDAP protocol, such as Microsoft Active Directory.
What is LDAP authorization?
After an LDAP-enabled client (which could be an individual user, an application or a network device) authenticates itself to an LDAP server via its username and password, LDAP authorization is the process of granting that client access to the resources it has permission for.
What is LDAP access control?
Access control is the granular management of user permissions to ensure that users get access only to the resources permitted to them based on their identity. As related to LDAP, access control capabilities restrict the resources can users access and the type of access they have to those resources.
What is an LDAP query?
An LDAP query is an operation — or "command" — that asks an LDAP-enabled directory service for information. For example, a user might query which accounts are set to expire within a month.








