In short:
- Many IIoT projects are stuck in pilot mode, evidenced by a new Bain survey that shows just 8% with “extensive implementations.”
- Municipalities are early adopters — and their “change some bulbs, add some cameras” model illustrates hidden costs of IoT.
- CFOs must work with CISOs and allocate appropriate budget for security tools, processes and training.
How are you feeling about your industrial IoT initiative?
If you mumbled, “What IoT initiative?” under your breath, that sums up where many manufacturing firms fall as we close 2019.
A recent Bain & Company survey(opens in new tab) of 627 executives, more than half of them in industrial roles, found IoT uptake going significantly slower than predicted in the advisory firm’s 2016 industrial IoT study. Long-term expectations are still high, but short-term forecasts are not quite as rosy.
The reasons will be familiar to manufacturing CFOs: high cost to implement, significant required structural changes and a dizzyingly broad array of supporting technologies with attendant integration and standards concerns.
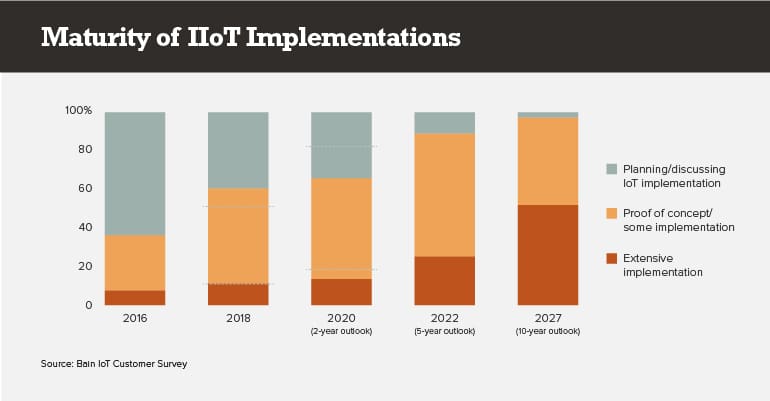
In 2016, about 8% of Bain respondents said they had extensive IoT installations. That number climbed to around 10% in 2018, but then growth stalled. By 2020, the analyst firm’s expectation is that less than 12% of respondents will have what they call “extensive implementations.”
It’s not until 2027 that extensive implementations crack 50%. That means you have time to gain the big benefits of IIoT, including improved quality control, asset tracking, monitoring and maintenance as well as better uptime and lower operational costs.
In fact, that potential is part of the problem, especially for cash-constrained manufacturing firms: Initiatives with big promise usually come with big price tags and long implementation cycles.
CFOs might remember the hype that surrounded IoT seven or eight years ago, when Cisco declared(opens in new tab) it a $19 trillion opportunity by 2019. Now, McKinsey & Company says(opens in new tab) we’re still six or seven years away from turning that first trillion, with estimates in the low trillions by 2025 — and it used some liberal accounting to make those numbers add up.
So how did Cisco get it so wrong? And who could have seen the hype train derailment coming?
Cisco failed to factor in the enormous changes in mindset required before projects could get needed investment and therefore reach scale. Realizing the benefits of IoT takes money, a lot of it, a hard ask as manufacturers see slowdowns and global uncertainty. Project scope, particularly in industrial settings, is typically very broad; you’ll spend a lot before you see real results. “Dipping a toe in” is difficult and frankly not all that revelatory.
Manufacturing CFOs can envision the benefits of collecting shop-floor data from hundreds or thousands of sensors. But moving from that vision to real-time control is a big leap. To a great degree, all-in on IIoT means disrupting a few hundred years of how manufacturing works. Automation is just as scary as it is alluring.
Challenge 1: Getting an IIoT project from edge-savings to game-changing benefits.
The “change some bulbs, add some cameras” model is popular in IoT circles thanks to an early embrace of the technology by cities from Austin to Zurich(opens in new tab) . A typical use case is switching to LED-based streetlights, which use 75% less energy than their predecessors and are often equipped with sensors and radios to further manage power consumption. LED bulbs also have much longer lifespans, reducing long-term maintenance costs.
ROI for the switchover is easy to quantify, so planners like those in Chicago(opens in new tab) often tack on surveillance cameras in areas with high crime or congestion. The cost to retrofit is a bit over $1,800 if you’re attaching a camera, about one-third of that to change out the light and add some networking. Over the course of 10 years, Chicago expects to save $100 million in power and maintenance, after covering the cost of the retrofit.
Sounds great, until you look at what’s involved in collecting data for analysis. Say the city puts cameras on one in 10 of its streetlights. That’s 27,000 video streams at, say, a 1-Mbps connection per pole. To store the video for a year, figure on paying for 1.7 PB of space and the associated computing power to crunch all that unstructured data. Planners could get insights on traffic, crime and more. But that legit big data opportunity will be expensive to capitalize on.
As with streetlights, your assembly line might need some modernizing. Selecting equipment that’s outfitted with sensors and networking capabilities is reasonable — the incremental expense is typically small compared with the cost of the equipment itself. However, you might not save money, improve quality or speed up production unless other areas of the assembly line are also brought into the IoT age so that you can apply end-to-end analytics.
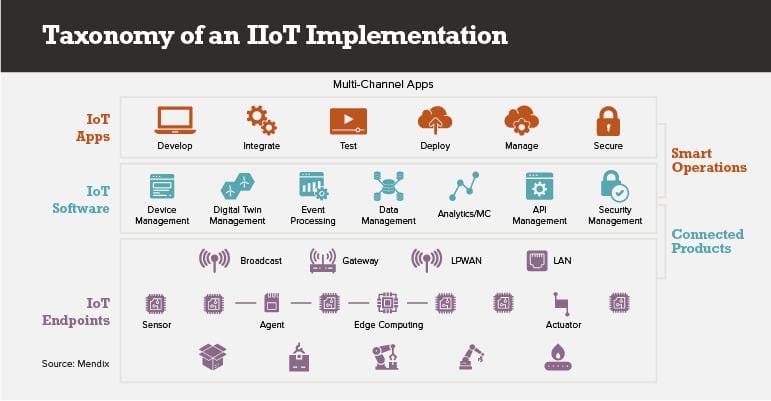
The diagram below shows what comprises a working IoT project. Of course, you need only the appropriate endpoints outfitted for your application, but at the other two layers, you need most or all of what’s listed. Typically, no one supplier does all this well, though some, like GE, Siemens and Hitachi, try.
What’s your response when the IT team says it needs data from component X to optimize a process, but there are no immediate plans to upgrade that component?
Industrial components are reliable, with lifetimes reasonably measured in decades. For CFOs, requests to retrofit ahead of plan will understandably prompt the question, “Aren’t there other ways to get at this data?”
Often, there are. They aren’t real time and don’t collect as much detail, but they may deliver some performance improvements, or at least more visibility.
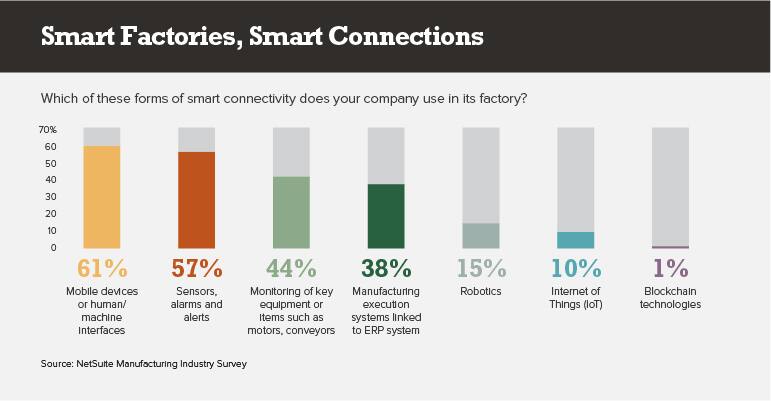
That, “Can’t we get to good enough?” stance was evident in our own survey of 109 manufacturing financial executives. Twenty-eight percent of our respondents hail from companies with annual revenue of $10 million or less, while 44% bring in between $11 million and $50 million. Respondents are acutely interested in data collection and analysis, but less open to overhauls to get at those insights. Just 10% have IoT initiatives in process, with an additional 30% saying they have projects in mind. Few are interested in new capital-equipment projects. Rather, they’re envisioning, for example, replacing workers’ clipboards with mobile devices that can capture data in a repeatable and automated way. Some 61% are doing such modest updates now.
CEOs may be less averse to capital spending. But whether IIoT is where they’d put that money versus, say, tooling up to create a new product line is a harder question. We asked survey respondents what they thought drove success in their organizations. Answers fell into three distinct classes: Product and service innovation ranked high, investing in new equipment and software ranked low, and data collection and organizational change landed in the middle.
This is not to say IIOT spending isn’t happening. But it does seem to be concentrated in larger companies that have teams to do the required integration and data analysis and that can justify the cost of stem-to-stern overhauls.
Challenge 2: Platform proliferation and compatibility costs dwarf hardware acquisition. But without integration, there is no automation.
The lesson of the internet seems lost on those vying for control of the IoT market. That is: Adoption of a single underlying protocol lifts all boats. There are hundreds of large IoT suppliers, many pushing proprietary platforms and ecosystems. The major operational technology players we mentioned above are joined by Amazon, IBM, C3, Cisco, Microsoft, Oracle, PTC and others in offering platforms that seek to underpin and coordinate all the functions that make up an IIoT system. While most have some limited integration points to other platforms, the goal is stem-to-stern use of their products.
The reasoning: Turning manufacturing control system functionality over to a third party comes with all sorts of issues, not least a perceived loss of customer intimacy. If IBM software controls your Hitachi robots, do you think of it as a Hitachi system or an IBM system? If the latter, does it matter if you buy Hitachi or Fanuc or some other brand of robot?
In fact, integration through software development kits, development tools and APIs is high on the list of selection criteria for the Top 10 IIoT platforms, as ranked by IoT World Today. But the reality is, true cooperation is rare.
Our advice for mid-tier manufacturers is to narrow the field to a few IoT suppliers that fit your needs and can tell a reasonable story on integration. Your larger peers will likely end up with multiple platforms at every layer, resulting in the unenviable and expensive task of integrating the integrators.
There are some open standards that allow for fiefdoms at one layer to work with those at other layers.
At the shop-floor level, OPC-UA(opens in new tab) , The Open Protocol Consortium’s Universal Architecture, seems to be gaining traction with manufacturers looking to get data from machines on the floor to analyzers further up the chain. The OPC began working to solve the machine-to-machine communication issues in the ’90s, well before M2M was a thing. The basis for its technology is a Microsoft standard called Object Linking and Embedding (OLE), a way to exchange object-level data between dissimilar devices and operating systems.
Standards at other layers provide some visibility(opens in new tab) , but visibility isn’t the same as control, and without control, there isn’t automation. And in fact, for years it’s been evident that few manufacturers are going to go through the wholesale upgrade and retrofit required to realize automation and other high-level IoT benefits. One area that seems more promising, however, is predictive maintenance.
Who wouldn’t want equipment to self-diagnose impending failures, asks Bain(opens in new tab) ?
It’s a significant leap, though, to trust predictive maintenance systems to the point where you forego or spread out regular tune-ups. Downtime is off-the-charts expensive, so manufacturers tend to hedge and keep to existing maintenance schedules. Thus, there’s an ROI problem.
Challenge 3: IIoT upsets the balance between information and operational technology.
For many industries, the convergence of IT and OT has delivered benefits. IT is great with data, OT has the manufacturing chops; get them working together and you’re on your way to Industry 4.0 nirvana(opens in new tab) . It’s like chocolate in your peanut butter... unless you’re on the OT side of the house. Then a better analogy is vinegar in your coffee.
OT systems run for months and years, they don’t get breached, they perform as predicted and they’re comparatively understandable. Chiefs of operations look at IT and see hacked databases, blue screens of death, lost data, failed upgrades and systems so complex that they know their IT brethren don’t fully grasp the nuance of how they work — because, try as they might, IT can’t address that list of faults.
For IIoT, data people talk about all the insights they’ll surface by adding sensors and higher-level controllers to operational technology. OT people listen intently and then ask about the operating systems these devices use. When they hear they’re based on Windows and Linux, you can understand the impulse to tap the breaks. You simply don’t reboot a forge or punch press or smelter. Monitoring? Maybe. True control? Not on your life.
It’s taken almost a decade and lots of proofs of concept for OT leaders to understand the benefits and get comfortable with the technology being brought onto their turf. It’s also taken that long for OT vendors to up their software games.
OT also thinks differently about technology cycles. Some elements of manufacturing haven’t changed much in 30 years; once analog controls went digital, further innovation at certain points was limited. The CIO is comfortable with operating at the speed of Moore’s law, and that’s not comfortable for operations experts.
Capital-intensive manufacturing equipment lasts a long time, so if we mark 2011 as when we started serious discussion about industrial IoT, it’s not at all surprising that widespread adoption is just now taking off. In that time, operations vendors like Siemens, Schneider and GE have invested heavily to improve their software systems and connectivity, which is good news for manufacturers.

Challenge 4: IoT security experts are raising alarms, and businesses are listening.
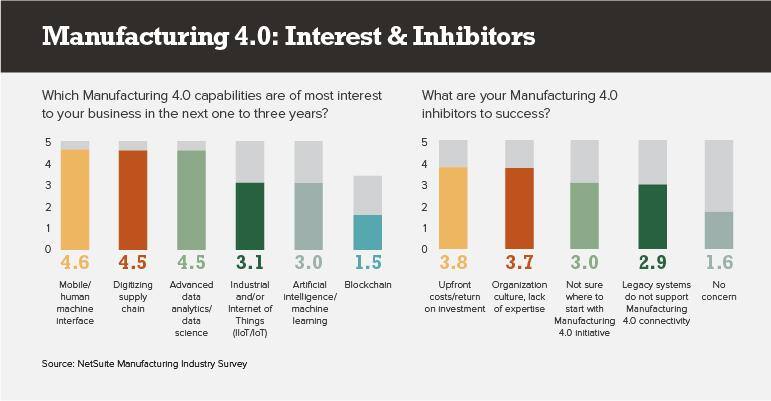
In its survey, Bain found security, uncertain ROI and integration issues are top IoT inhibitors, along with concerns over technical expertise, data portability, and vendor and transition risk.
Some of these you’ll iron out during a proof of concept. Security, however, is only growing as an area of concern(opens in new tab) . Before IoT, operational security meant the fence around the building, the lock on the door, the cameras around the premises monitored by guards and the fact that nothing was connected to the internet. Manufacturing networks, where they existed, relied on an air gap between the shop floor and the rest of the world.
Gartner projects that by next year, 25% of attacks on enterprises will leverage IoT in some way. The analyst firm goes on to point out that only 10% of security spending is focused on IoT. Sensors, with their small-footprint operating systems and lack of regular firmware updates, are popular launching points for attackers. So as with OT/IT convergence, learning to trust that a shadowy figure in a hoody isn’t going to send the manufacturing floor into a tailspin is a process.
CFOs need to address a few areas with their CISOs:
- The firewall between the manufacturing floor and the rest of the enterprise needs to take a deny-by-default(opens in new tab) approach, with specific ports opened only as needed for data transmission in both directions.
- Shop-floor security needs a different mindset than security in the rest of the company. If shop-floor workers need access to the company LAN, that should require a separate login from any systems they access on the floor.
- Wireless networks must be isolated, and no device should be on multiple networks, except for firewalls. Likewise, admittance to shop-floor wireless networks needs to take a deny-all stance, with only whitelisted devices allowed. That means more work for administrators, particularly given the number of IoT sensors that will eventually inhabit your manufacturing line. There will be a delay in getting new devices online, which implementers will complain about, but that’s the cost of security.
- Most breaches are the result of human error, so as an IIoT implementation proceeds, make sure security education and training keep pace.
- Your device manufacturers want to deliver software patches and upgrades over the internet. If you do allow auto-updates, you open yourself to so-called man-in-the-middle attacks, where a third party gets between your device vendor and your shop-floor network. If you don’t, keeping IoT devices patched becomes a manual, expensive and time-consuming process.
- Budget for new security processes and tools and potentially, an expert outsourcer to install and configure them. Anomaly detection systems are a good idea, but you also need a hard-nosed approach to device tracking and network admittance. If a critical piece of equipment is left off the list, processes could fail, at worst. At minimum, they will not be part of data collection and process visibility.
- Analyze risk exposure at every step of an IIoT implementation — and don’t just accept the CISO or contractor’s word that everything is locked down. Penetration tests(opens in new tab) are audits for security. Run them regularly.
IIoT security is manageable, if you plan and budget for it at every stage of project development. And as with integration, the most painful learning and subsequent product hardening will be paid for by large-enterprise early adopters.
Challenge 5: Delivering on the ROI promise.
As you might expect, most operational technology companies are not strong in analytics. That truly is the domain of IT powerhouses like Amazon, IBM, Microsoft and PTC. ROI doesn’t happen until you get those instrumented OT systems at least feeding data to the IT analytics engines and those systems start revealing real-time information you couldn’t get another way.
For CFOs, this an uncomfortable position. The net present value of a project(opens in new tab) that takes longer than eight years to bear significant fruit starts to approach zero even with today’s low interest rates — in other words, there must be a better way to invest that money. This is why mobility-based data collection projects look so good. The benefit is clear, you’ll have better and more actionable data, and you can get the project turning out results in a year or two.
For many shops, including those in our survey, it’ll likely require another generation of OT capital expense to realize IoT benefits. In that time, as with security, large manufacturers will have necessarily worked out most of the integration kinks, and later adopters will benefit from that work.
Some pundits dismiss dashboards as a half-hearted step toward IoT ROI. There’s some truth to that — dashboards(opens in new tab) don’t deliver control abilities. But they are a way for your operational team to gain visibility into the insights new sensor arrays can yield and comfort with how analytics engines will process data.
While proof-of-concept projects have been labeled a purgatory from which many IoT initiatives never emerge(opens in new tab) , it’s worth figuring out first steps and staying informed on what your competitors and suppliers are doing. Any systems you purchase should have sensors and networking built in so that when you turn the ROI corner, these components are ready to play their parts.
Art Wittmann is editor of Brainyard. He previously led content strategy across Informa USA tech brands, including Channel Partners, Channel Futures, Data Center Knowledge, Container World, Data Center World, IT Pro Today, IT Dev Connections, IoTi and IoT World Series Events, and was director of InformationWeek Reports and editor-in-chief of Network Computing. Got thoughts on this story? Drop Art a line.