What information is an employee or a user allowed to access? This question can be surprisingly complex, especially for organizations employing hundreds or thousands of people. Considerations for how best to decide, manage and track who has access to information and applications varies by business, industry and company size. Managing authorization well helps your company stay secure and compliant while providing the information and programs employees need to get their work done.
What Is Authorization?
What do you mean by authorization? Authorization determines the level and type of access to resources that a user has. It answers the questions who can do what with your data and applications. Once a user is authenticated (more on this later) with their user credentials such as username and password, their Authorization will determine the predetermined menu of operating systems, applications, functionality and the level and ability to make changes to underlying data. Collectively, these permissions are known as client privileges.
In most organizations, the authorization structure is not flat. Authorization does not grant access to every resource. Instead, different employees have access to different resources. Companies use various processes to determine which employees can access a resource based on what they need to do their jobs. By restricting access to certain materials, businesses have a way to protect their most critical data – including intellectual property, consumers' identity, medical records, payroll information and more. Additionally, it can be a tool to help employees find the resources and information they need more quickly without having to wade through every company document and folder. Generally, organizations follow a principle of least authority when granting access to information. This approach ensures that users and employee only have access to information that is required for their role and nothing more than that. The damage a potential bad actor can do is minimized.
Key Takeaways
- Authorization is an essential best practice for both security and compliance.
- Not only does authorization protect your information, but it also preserves the privacy of consumers and can shelter companies from fines resulting from compliance violations.
- Although authorization is not necessarily easy in large organizations, the proper access control process can help mitigate this difficulty and protect users, data and customers.
- Follow principle of least authority when establishing authorization parameters.
Authorization Explained
Why do we need authorization? There are two primary reasons. First, you want to protect your business information from bad actors both inside and outside the company. If an employee misplaces or has credentials stolen, controlling what data may be vulnerable is important. One goal of authorization is to ensure that each employee has access only to systems and information they need to do their jobs, and not to all business data. This way, if thieves manage to steal credentials, they'll be limited in how much information they can access.
The second reason deals with compliance. For example, the Health Insurance Portability and Accountability Act (HIPAA) requires that documents such as medical records need to be kept private. Not all employees should have access to patient information, and those who do will need to undergo regular trainings and that information will need added layers of security.
If the U.S. Department of Health & Human Services (HHS) finds employees or others have improperly accessed or exposed patient records, HHS can levy fines against the organization for this compliance breach. By limiting access, providing training and closely monitoring access to confidential information, health care organizations can protect patients while also avoiding fines and legal liability. Many other organizations, including those outside the health care space, are subject to similar controls. For example, schools and companies that work with students are governed by similar rules under Family Educational Rights and Privacy Act (FERPA), which protects the privacy of student records. Other information you need to protect includes private employee information, such as social security numbers, and customer information, such as credit card numbers.
How Authorization Works
At its most basic level, authorization is allowing access to certain applications and information with a username and password. A user might be authorized to access a word processor, an email client, a CRM and more. With basic authorization, users would have a distinct user ID and password for each system. For example, your employees might need one log in for the CRM, another for their email, another to access a server, and so on. When they need access to new systems or information, they send requests to an administrator, who reviews the request and then provides an additional login credential.
Basic authorization has some challenges.
- It doesn't scale. As the company grows, manually tracking which employees have access to programs and information becomes an unsustainable burden for administrators to do manually.
- It's not convenient. Without a single log in service, your employees have to recall multiple separate usernames and passwords just to go about their work. This can also result in insecure behaviors such as writing down passwords on post-it notes.
- It's not secure. Suppose a user needs to make an access request to access a single financial record. With basic authorization, the administrator may have to turn over access to the entire database to that employee and then remember to revoke access later. This can pose security and compliance issues, depending on the information that’s stored.
Robust authorization protocols have systems to quickly and automatically generate client privileges for employees, single sign-on systems and offboarding processes that automatically terminate temporary access to essential systems once it is no longer needed.
Authorization vs. Authentication
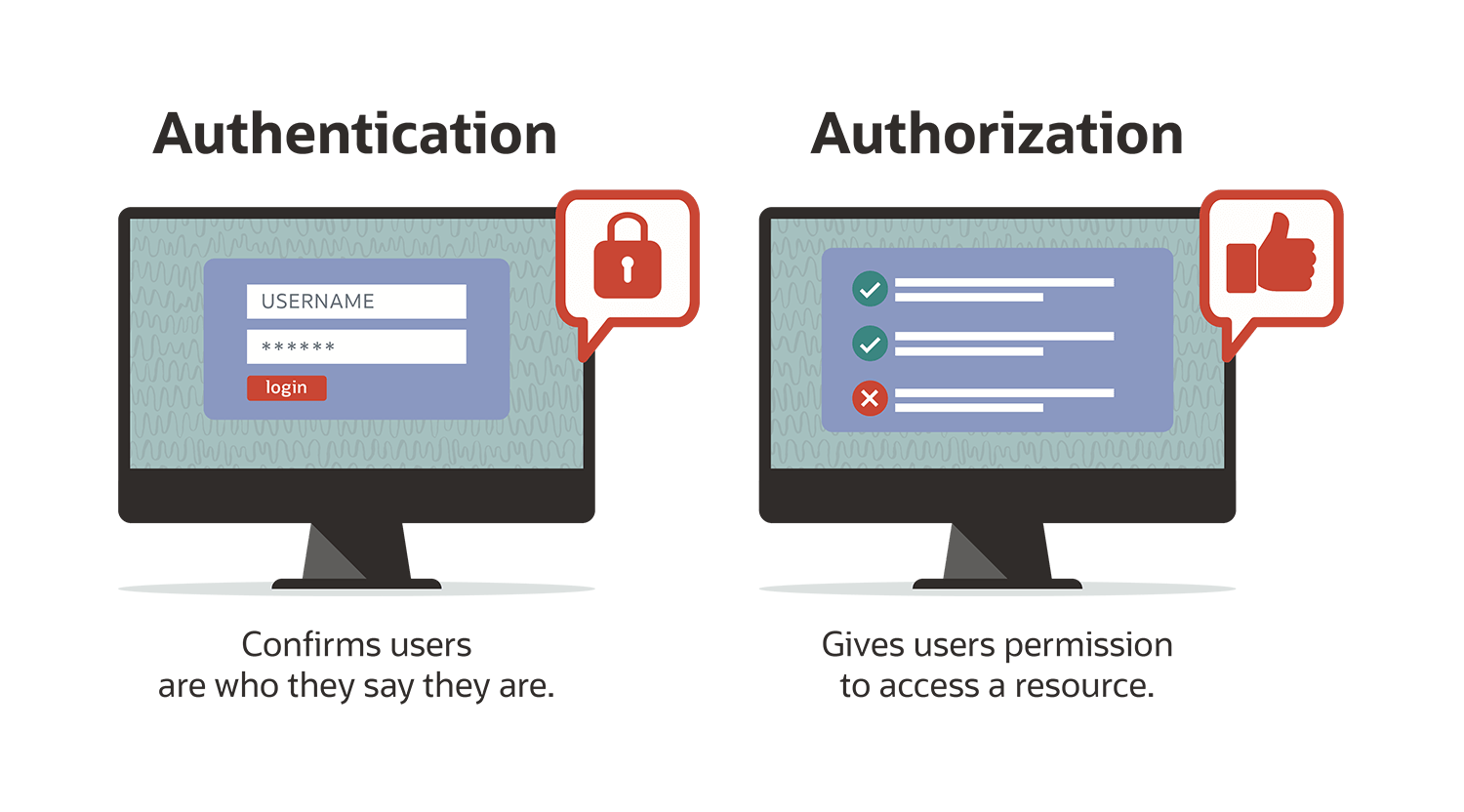
Authentication and authorization are often used interchangeably — but there are some important differences. Authentication is a way for users to verify they are who they say they are. This can be done through usernames and passwords. And increasingly popular is two-factor authentication. This requires not just a username and password, but also another layer of security through another device, most often via a phone app or a texted code to a user’s phone. Authorization follows authentication. Just because users are authenticated, this doesn't mean they receive access to all applications, services and data within the corporate network. Instead, they only get to access the resources that they are authorized to use.
The two steps of access control, authorization and authentication, are both necessary for a user to interact with a corporate network. If users aren’t authenticated, they can't use any services because they can't get into the network. If a user isn't authorized, they won't be able to use any services even if they're authenticated.
Why Use Authorization?
Authorization is used for security, compliance and operational reasons.
It’s vital to information security because it represents one of the innermost components of a concept known as "defense in depth." The idea of defense in depth is that a company should place many information security applications — firewalls, monitoring tools and identity management, to name a few — around the corporate network's perimeter. If an attacker evades one application, other applications still have a good chance of mitigating their attack. However, even defense in depth can be thwarted if employee credentials are stolen. But if each employee only has access to a small and relatively unimportant amount of data, an attacker needs to steal multiple credentials to pull off a meaningful attack. That gives them a much greater likelihood of being caught and stopped.
One of the best illustrations of authorization for compliance reasons is HIPAA, which is meant to protect private patient data. But other industries need to maintain compliance in protecting confidential information, such as customer and employee data. If things like credit card numbers or personal employee information are left vulnerable, your company could be held liable for damages, not to mention potentially losing valuable team members or customers and bad PR.
Authorization is also a key component of operations for many workplaces. Making sure your employees have enough information to get their jobs done, but aren’t bogged down with the entire company data sources, can help improve worker efficiency. And a single sign-on can make it easier for them to access necessary information and resources, as well as make the authorization more secure.
Authorization Use Cases
Preventing unauthorized employees from looking at critical data is another reason why authorization is essential. HIPAA is an excellent example of why it is critical, but let's look at a few more examples of what the process looks like in the context of compliance.
Offboarding former employees
Not every employee leaves on good terms with an organization. If employees think they've been terminated unjustly, they might try to steal valuable information on their way out the door. Businesses can use authorization processes to automatically terminate corporate account access after parting ways with personnel.
Working with vendors and contractors
Businesses often need to share information with third parties. For example, a business may be working with a managed service provider to migrate its applications to the cloud. Here, the MSP would need to access their applications and data. With authorization, businesses can assign client privileges to vendors, allowing them to view this information and move it around but preventing them from editing or deleting their data.
Diminishing privilege creep
Privilege creep means employees are gradually accruing permissions they don't need. For example, suppose an employee transfers from sales to accounts payable while retaining her sales permissions. This employee may still have access to the CRM, even if she no longer needs it. That makes the employee a potential security risk – if her credentials are stolen, it opens the business up to even more vulnerabilities. Using up-to-date processes, administrators can detect if employees have permissions they don't need and then roll them back.
Authorization Approaches and Methods
Authorization is used in many contexts to defend businesses and their critical information, but how is it accomplished? There are several methods, each with its advantages. The overriding goal is to make it easy to manage enterprise-wide authorization while making it difficult for employees to accumulate permissions that they don't need.
Token-based authorization
One of the primary concerns of managing authorization without a single sign-on is that employees often find it inconvenient, and they'll think of ways to work around it when necessary. For example, imagine employees needed to re-enter one of several different passwords every time they left their computer or navigated away from a website. They'd probably find their productivity to be slow, and they'd be tempted to resort to insecure practices.
With token-based authorization, the user only needs to log into an application once. In exchange for their credentials, they receive a token from the system. The token takes the form of a small text file that's stored in the user's browser. As long as the user continues to store that token, they can stay logged into the service without re-authenticating.
Role-based access control (RBAC)
Token-based authorization works well, but it's usually used in conjunction with other systems. How does an administrator understand which systems to grant an authorization token? Often, they do this using role-based access control (RBAC).
RBAC rapidly assigns permissions to new and existing employees based on their role in an organization. With RBAC, you start by creating a predetermined list of every position within the company and then deciding what resources this position should access. There's no need to spend time wondering which permissions an individual employee should have once they're hired – that decision has already been made.
This method is common among companies with large numbers of employees, but it can have drawbacks. For example, if an employee needs access to a new resource, the administrator needs to handle that request individually. It isn't easy for a large company to process these requests promptly and then revoke access once it's no longer needed.
Access control lists (ACLs)
RBAC works by determining which applications and files a given role should have access to and then placing users within these roles. Access control lists (ACLs) work in reverse. Instead of starting with a role and then appending a list of applications that the role can access, ACLs start with the applications and files.
Let's say that a user — call him Bob Smith — wants to log into a database. After Bob authenticates his credentials, the application checks its embedded access control list to see if Bob's name is there. If Bob's name is on the list, then he can access the application.
In some cases, RBAC is somewhat easier to use than ACLs because it can be challenging to go to every application in an organization and add a user's name to a list if he or she is allowed to use it.
ACLs have a security use case when it comes to the network perimeter. Since ACLs can be applied to infrastructure, such as routers, administrators can place ACLs on routers controlling the network's edge. Here, the ACLs don't just control which credentials are authorized to access the network – they also act as traffic filters. Based on characteristics such as the IP address and port number of incoming packets, the ACL can accept or deny specific traffic, adding to the network's security as a whole.
Authorization Examples
What is authorization? Here are a few examples. These include somewhat rare methodologies compared to token-based authorization, RBAC or ACLs, but they may become more prevalent in the coming years as companies look for better authorization methods to improve security.
Attribute-based access control (ABAC)
With this process, users are directly associated with an attribute that grants them access to a resource. One commonly used example is a secure USB key. Possessing a secure USB key is an attribute, and having one can grant access to sensitive files and applications within an organization.
Mobile access control
This control is much like ABAC. Except, instead of possessing any attribute, the attribute in question is possessing a smartphone. Specifically, the user downloads a mobile credential application and then uses their smartphone to authenticate. Their authorizations store on their device as well. An example of this would be using a phone to make a mobile payment — tapping a phone on the pin pad authenticates the users’ credentials, which then authorizes them to exchange money for goods and services.
Graph-based access control (GBAC)
Here, instead of configuring access by employee or role, permission is configured at the objects level such as files and applications. Access rights generate using a query language instead of exhaustively listing the permissions assigned to each role, which reduces workloads.
NetSuite offers a flexible and highly customizable access control system compatible with whatever authorization process administrators have in place. This system promotes security and compliance, allowing you to focus on core competencies while protecting users and customers.
#1 Cloud ERP
Software
Authorization FAQs
How is authorization used?
Authorization is used in conjunction with authentication. Authentication occurs when users input their credentials, like a username and password. Authorization is what users get in exchange – access to various files, applications and services.
How does authorization work?
Permissions are added to predetermined roles in a widely-used form of authorization known as role-based access control (RBAC). Once a user is assigned to a role, they receive all the permissions that their role entails.









